Enterprise Configuration
Administration > Configuration > Enterprise Configuration
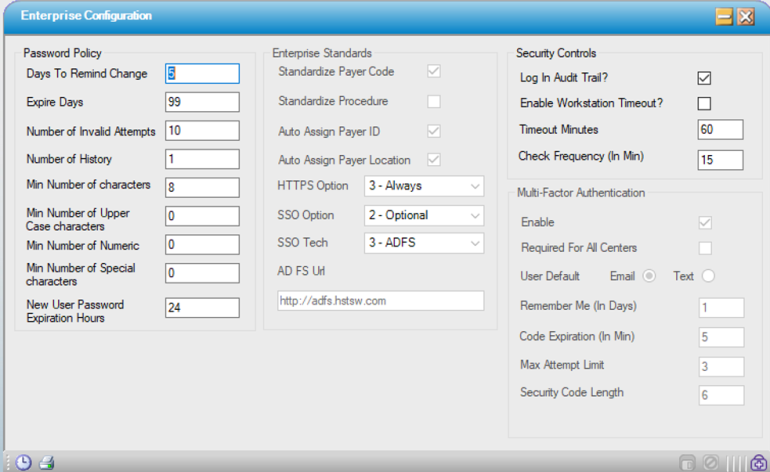
Password Policy
| Option | Description / Action / Rules |
| Days to Remind Change | This number determines how many days prior to expiration a user will be reminded to change their password. |
| Expire Days | This number determines how often a user will be prompted to change their password. |
| Number of Invalid Attempts | Exceeding the number of invalid attempts set here will result in users being locked out of the system. |
| Number of History | This will control how soon users can reuse a previously used password. The number entered is the number of passwords between. |
| Min Number of characters | Determines the minimum number of characters a password must contain. |
| Min Number of Upper Case characters | Determines the minimum number of upper case characters a password must contain. (Can be set to zero.) |
| Min Number of Numeric | Determines the minimum number of numerals a password must contain. (Can be set to zero.) |
| Min Number of Special characters | Determines the minimum number of special characters a password must contain. (Can be set to zero.) |
| New User Password Expiration Hours | Determines how soon the system generated password created for a new user or due to a password reset will expire. |
Enterprise Standards
These settings are Administrative functions that must be set up by an HST Account Representative, preferably when initially creating the database.
| Option | Description / Action / Rules |
| Standardize Payer Code | If checked, Centers will share Payers in each center that is on the same enterprise database. Users will see two separate menu selections for Payer and Configuration. |
| Standardize Procedure | If checked, Centers will share Procedures in each center that is on the same enterprise database. Users will see two separate menu selections for Procedure and Procedure Configuration. |
| Auto Assign Payer ID | If checked, system will generate numbers for the Payer ID in sequential numeric order 1,2,3, etc. |
| Auto Assign Payer Location | If checked, system will generate numbers for the Payer Location in sequential numeric order 1,2,3, etc |
| Auto Assign Payer ID | If checked, system will generate numbers for the Payer ID in sequential numeric order 1,2,3, etc. |
| Auto Assign Payer Location | If checked, system will generate numbers for the Payer Location in sequential numeric order 1,2,3, etc |
| HTTPS Option: |
Drop down allows selection of: 1 - None 2 - Optional 3 - Always |
| SSO Option |
Drop down allows selection of: 1 - None 2 - Optional 3 - Always |
| SSO Tech |
Drop down allows selection of: 1 - None 2 - Kerberos 3 - ADFS |
| ADFS Url | Active Directory FSMO url can be added. |
Security Controls
| Option | Description / Action / Rules |
| Log In Audit Trail?: | If checked, this tracks who logged in, when, and whether they attempted to use an invalid password. This is intended for IT staff to conduct security audits. A query can be run to return results upon request. |
| Enable Workstation Timeout? | Check the box to enable automatic close of HST Practice Management after a predetermined period. Users will get a pop-up warning that HST Practice Management is about to close. Click "OK" to reset the timer; otherwise the application will close upon timeout. |
| Timeout Minutes | Number of minutes of inactivity before HST Practice Management application closes. |
| Check Frequency (in Minutes) | How frequently the system will check for activity. |
Multi-Factor Authentication
These settings are Administrative functions that must be set up by an HST Account Representative.
For complete instructions on configuring MFA, refer to the Configuring Multi-Factor Authentication help file.
| Option | Description / Action / Rules |
| Enable |
This check box defaults to OFF and when its OFF Multi-Factor Authentication cannot be used for any Center in the Enterprise When this check box is ON, all Multi-Factor Authentication options become enabled so an the rest of the settings can be configured. Please review the Before You Begin help file prior to having this feature enabled. |
| Require for All Centers |
This check box defaults to OFF and is optional. This option defines if all Centers are automatically opted in for MFA or they can be opted in individually. When Require for All Centers is OFF and Enable is ON, each Center in the Enterprise can access Center Configuration and turn MFA ON or OFF for the Center without HST Support intervention. When Require for All Centers is ON and Enable is ON, all Centers are automatically Opted in for MFA and it cannot be turned OFF at the Center Configuration level. See Center Configuration for more details. This option allows Enterprise Administrators, where there are many Centers, to turn on MFA at each Center incrementally to help to avoid a large influx of calls to their help desk for user access issues. See the Before You Begin help file for information on rolling out M-FA. |
| User Default |
This is required and can be either Email or Text. This option will default to Email when MFA is initially configured. This option acts only as a default setting for the user for their first time log in after MFA has been enabled for the Enterprise to which the user is logging in. For example, if this setting is Email and the user does not have a viable email upon first attempt to log in after MFA is enabled, the system will automatically change the user’s default to text. If they have no viable option for MFA authentication, then the user will not be able to log in. “…Using a phone number as the primary way to prove account ownership is faster than email and more accurate.” 1 |
| Remember Me (In Days) |
This is configurable, required and the value must be greater than zero (0). The default is 30. This option defines how long the user will be remembered in days before needing to re-authenticate upon log in. This will only be enforced for users who have permissions to Centers in the Enterprise that have MFA set to ON at the Center level either by manually enabling the Center MFA option, or by automatically opting in all Centers by using the Require for All Centers above in this section. |
| Code Expiration (In Min) |
This is configurable, required, defaults to 10 and the values must be a number, 1 through 99. This option defines the number of minutes the One Time Passcode (OTP) can be used before it expires. If a code expires, the user needs to get a new One Time Passcode code by clicking the Resend button on the Authentication dialog or attempting to log in again which would generate a new OTP. See Authentication Dialog for more details and using the Resend button. |
| Max Attempt Limit |
This is configurable, required and the value in this field can be a number from 1 through 10. The default for this field is 3. This option defines the number of passcodes the user can get before their account becomes locked. Once the Max Attempt Limit has been reached, their account is locked and can only be reset by another user that has access to User Profile > Password Reset. See the Unlocking Accounts help file for details. |
| Security Code Length |
This is configurable, required and the values can be a number from 6 through 10. The default is 6. This option defines the length of the One Time Passcode. “…The most common method for confirming a working [mobile] number belongs to the account holder is by sending a one-time code—usually a 4-to-6 digit token—via SMS and asking the recipient to enter that code back into the application. Using a phone number, in conjunction with two-factor authentication (2FA) at log in, ranks high among the options to increase the protection of user accounts and reduce the cost of fraud to the business.”2 |
Foot Notes:
1 Twilio. https://www.twilio.com/hub/strong-customer-authentication-best-practices-using-phone-numbers-protect-your-users
2 Twilio. https://www.twilio.com/hub/strong-customer-authentication-best-practices-using-phone-numbers-protect-your-users